After getting my hands on a WiFi Pineapple (a post on this to follow!) and enjoying exploring its features I quickly realised my mobile device is super promiscuous when it comes to joining open access points I’d previously connected too (Premier Inn, McDonalds etc). This got me started on looking into VPN solutions and after looking online one particular VPN provider seemed to crop up a lot – Private Internet Access (PIA for short). Now there may be others out there not part of the “fourteen eyes”, or have better “no logging” policies but this isn’t a concern of mine as I just wanted to ensure traffic was encrypted between my device and the endpoint to prevent snooping in public locations. On my Android device the app was easy to configure and worked fine, but I figured I had another 4 devices I could install the client on and wondered if I could do something with my Sophos XG to tunnel all traffic from my home.
Unfortunately the Sophos XG doesn’t provide connectivity options for PIA’s VPN service, which relies on OpenVPN for such connections. What I could do however was setup a pfSense appliance to use it’s OpenVPN client and position this in front of the Sophos XG.
Now I still wanted inbound SSL VPN traffic to the Sophos XG when I was away from home and wanted access to files and so on, but outbound I wanted HTTP and HTTPS traffic to be encrypted in the VPN tunnel from the pfSense box.
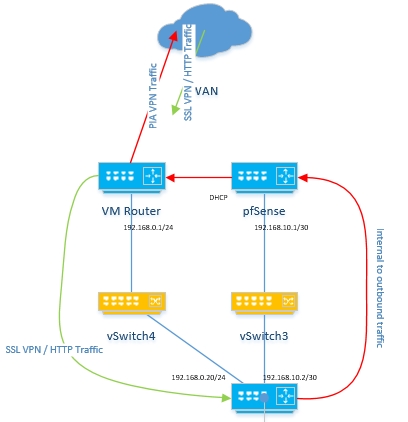
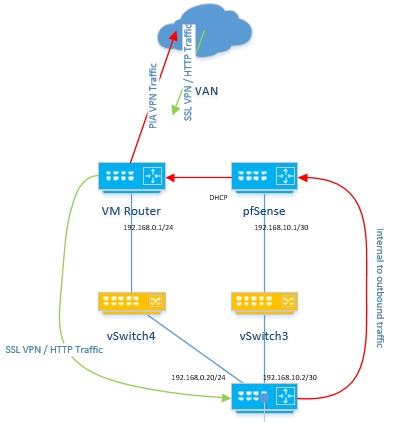
My first step was to download the pfSense image and install it as a Virtual Machine on my HP Micro Server. The install was straight forward and there were many guides to setup pfSense with PIA’s VPN online including PIA’s own website. It’s also possible to setup a kill-switch if this is something that you’re looking for.
Once I was happy the pfSense box was establishing a VPN tunnel successfully I then created a new vSwitch to connect a “LAN” vNIC of the pfSense VM to a new “WAN” vNIC on the Sophos XG VM. This meant the pfSense had a outside link connected to the DMZ network on a DHCP address with no port forwarding as well as having an inside link to the Sophos XG appliance on which would carry the traffic that was to be encrypted. The Sophos XG had two “WAN” links, one straight onto the DMZ with ports forwarded for SSL VPNs and a HTTPS website and another to the pfSense which would be the primary gateway for outbound traffic. A static route was also added to the pfSense to route traffic for the user LAN back via the Sophos XG.
The next step was to create a new policy rule on the XG to allow management of the pfSense as well as adjust existing rules to use the new WAN link as the primary outbound connection as by default it will attempt to load balance between the two WAN links.
All in all this didn’t take too long to setup and cost me only around £30 for a years subscription. Speed-wise, I’ve not noticed any slowdowns or any other issues aside from some initial dropouts of the tunnel, however I identified this was because I’d enabled logging against the tunnelled traffic on the pfSense which regularly caused the service to need a manual restart. Since I’ve disabled the logging there have been no instances of downtime. Below PRTG graphs show the before and after for pings and HTTP requests to bbc.co.uk:
Hi, I’m trying the same thing but I’m able to have 2 WAN IP at the same time.
How would you go about setting that up?
I’m new to Sophos some inputs are welcome..
LikeLike
Hi Morten,
So if I’ve understood correctly you’re wanting two WAN interfaces on the XG, with one being the “real” WAN and the other being a point to point between the XG and the pfSense. The 3rd NIC would be your LAN.
If that is the case and it’s virtual then you add an extra vNIC in your VI host for the XG VM, then probably a reboot of the XG for good measure to pick up the new NIC. Then head into Settings, Network, Interfaces and it’ll show as a new port probably with a DHCP address. Give it any IP (I used 192.168.10.2 /30) and assign the zone as WAN. By putting the zone in place, all rules should quite easily work with the new interface.
You’ll also want to head into WAN Link Manager and disable NAT on the new interface.
On the pfSense side, you’ll want to have just two NICs, one as the point to point and the other in the same “real” WAN as the XG. Follow the guides as linked to setup the VPN side of things, but also add in a static route to your LAN network that hangs off the XG to be accessible via next hop of the XG’s point to point interface (in my case 192.168.10.2/30). You’ll also want to bear in mind any NAT or ACL rules you implement on the pfSense to also include the LAN subnet.
Lastly, on the XG ensure you have some permit policies against HTTP and HTTPS traffic (or all other traffic you want to go via the VPN) which set the routing to go via the pfSense gateway (and if you want as a backup to use the normal WAN). The one thing this doesn’t allow is failover from the VPN to the regular WAN on the Sophos XG if the VPN goes down as it only monitors the link to pfSense itself. If you’re wanting that level of failover then you’d want to make some changes instead on the pfSense (read up about killswitches).
Hope that helps!
Mike
LikeLike
Thanks for the detailed information Mike! Do you not use our Sophos XG as a router or do you have another vm for that? I only have Sophos for everything so not sure I can use your guide but see what you are getting at. Want I ment was that I’m able to have 2 active WAN IP’s from my provider so my first thought was to have 2 wan active, one on each fw and just route the traffic to pfsense. And as your self be able to VPN in the Sophos.
Hope thats make sense.
If its easier to pm that’ll be okay for me, dont want to take up too much of your time!
Your way seems to be better if the case is what I think with a vm router in front of the two.
Thanks again
LikeLike