In an earlier post we used 802.1x to authenticate users into the network and assign them into a VLAN based on either a successful or unsuccessful authentication as well as a VLAN for clients who did not send an initial EAPOL message. While this can be quite useful, it can also be quite restrictive – what if we wanted different authenticated users into different VLANs rather than just the authenticated VLAN? This is entirely do-able. An example use case would be having be an office with several hot desks, used by various departments, but a compliance restriction that places heavy restrictions on network access into particular resources such as HR, finance and so on. It would be an administrative headache to keep logging into the switch each time to change the VLAN depending on who was sat at these hot desks for the day, so we can leverage 802.1x to do this for us.
If you’re reasonably new to 802.1x then I suggest you head over to my earlier post on 802.1x and return back once you’ve read it. It covers some of the fundamental concepts and configurations which we’ll build on here. To start with, we’ll want to configure our AAA settings but this time with one addition ‘aaa authorization network default group radius’ which will instruct the switch to use AAA for network services including VLAN assignment. We’ll also get away without stipulating a VLAN for the interface as this will be passed to the switch from the RADIUS server (although in production you may want to set this in case the RADIUS server(s) are unavailable).
aaa new-model
aaa authentication dot1x default group radius
aaa authorization network default group radius
dot1x system-auth-control
radius-server host 172.16.0.20
radius server key CiscoLab
vlan 20
name Staff
vlan 30
name Students
vlan 40
name Guests
interface GigabitEthernet0/14
switchport mode access
dot1x pae authenticator
dot1x port-control auto
spanning-tree portfast
On the NPS policy side we’ll add in the IP addresses of the switches as RADIUS clients with the RADIUS server key we setup earlier on the switch. We’ll then create a couple of new Network Policies for VLAN20, VLAN30 and VLAN40 with conditions against the Active Directory user groups we want to assign, with specific attention to the RADIUS Attributes section as we’ll need to use options 64, 65 and 81 to feed the VLAN options back to the switch. The below screen grabs show the process for VLAN40, but it is just a rinse and repeat for the other VLANs modifying the groups and VLAN ID where required.
NPS Policy
Once this is complete the last step is to configure a client machine for 802.1x wired authentication. I’ve covered this here, but in brief this requires the ‘Wired AutoConfig’ service starting on the Windows device.
Now onto testing…
Assuming you’re good to go for connectivity between the switch and RADIUS servers then we can move onto connecting our device to the network port we configured for 802.1x. Here I’ve connected in the device and given the credentials of an authorised student, as a result being placed in VLAN30:

In this example I disconnected the device, reconnected and gave the credentials of an authorised guest to be placed into VLAN 40 (Guest):

And finally, providing credentials that place me into VLAN 20 (Staff):
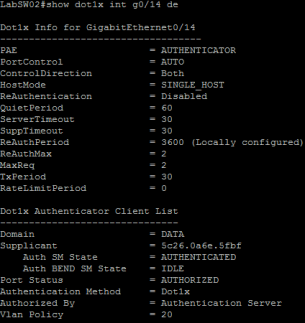
There are some extensions to this, we can incorporate a ‘dot1x auth-fail vlan #‘ command to take care of any devices that refuse to talk 802.1x with the switch. Anther useful extension of this is for approved devices such as printers we can use MAC Authentication Bypass to authenticate these devices by MAC address should they time out on the 802.1x process – I’ll cover this in a future post!




Great write up; however why does one have to configure the clients for 802.1x if there’s a mac auth mechanism in place? Mac auth should not require any client config; in fact it should work with non-computer devices like printers etc? Thanks
LikeLike
This way we can have a blanket config across all ports (should users be moving about) which also permits us to connect in printers and other non 802.1x devices without reconfiguring the port so long as the MAC is already setup in the RADIUS server side of things. Hope that clears things up?
LikeLiked by 1 person
That makes sense, Thanks!
LikeLike
Hello Mike,
Very well written by You. Thanks Alot
I test this and its working but there is one bug when we configure dot1x auth-fail vlan, the switch overwrite the vlan to PC but then after that even Login with authorized username switch never try to contact NPS.
After removing this command switch always contact NPS while login and logout time.
I want to configure like this that even after going to Guest vlan bu auth-fail switch should contact the NPS server while Login and Logout,
i think there is some special commands for this.
Thanks
LikeLike
Hi there.
I recall I experienced a similar issue in the lab due to timeouts. You can increase the retry attempt numbers and timeout values – I found “dot1x max-reauth-req” with a value of 3 to be successful.
Cheers
LikeLike
Hello, i have tried the same and see it is getting granted in the NPS. But not getting an IP in the laptop. Did i missed anything?
LikeLike
Have you confirmed by doing a regular static vlan and seeing if the machine gets an IP? It might be the vlan you’re trying to assign isn’t trunked to the switch.
You could also assign an svi on the edge switch with a DHCP address and seeing if that works.
LikeLike
Hello Mike,
Great Article, Can we make our switch as a radius server and then do mac to vlan mappings.
Also to how we can use non domain devices in Microsoft NPS server, like phones, Printers. Basically I want to dynamic assign vlans with respect to Mac-addresses only independent of usernames.
Thanks
LikeLike
Dynamic VLAN based on MAC address is covered here https://mikepembo.wordpress.com/2016/11/14/802-1x-mac-authentication-bypass-mab-to-an-nps-server/
LikeLike
Reblogged this on Konkretor Blog, IT Stuff and more.
LikeLike
There is not much on the internet about 802.1x Authentication. In my scenario, i have a SG500 switch with a Cisco WLC 2504 and Aironet 1852i. I am trying to use 802.1x Authentication to authenticate the access points against the SG500 switch since some of the access points are located in a public place and we want to protect the switchports from an unauthorized user removing an AP and plugging in directly.
I have not had success using the built-in RADIUS Server on the SG500 switch to service the 802.1x Authentication requests from the APs. It would be great if you could write an article on how to accomplish 802.1x Authentication on a SG500 switch using built in RADIUS Server.
Thanks for all your work.
LikeLike
Hi Michael,
So this isn’t a situation I’ve encountered up until you’ve mentioned this I’m afraid.
One option would be to put the ports where the APs connect into a single VLAN (not trunk) and make this VLAN as isolated as possible, with no internet or access to other VLANs. If someone connects their unauthorised device they won’t really be able to do much damage. The genuine WAPs however can connect and, using FlexConnect, all data from the different SSIDs is tunnelled securely to the WLC and broken out to their respective VLANs from there: https://community.cisco.com/t5/wireless-mobility-documents/wireless-lan-flexconnect-configuration-example/ta-p/3112924
The other option I can see would be to identify the MAC of the APs management interface and use MAC address bypass (https://wordpress.com/comments/approved/mikepembo.wordpress.com/860) for the AP’s MAC address to permit access. The MACs of connected devices to the AP would still be permitted as the MAC of the AP itself acted as a ‘key’ opening the port up for traffic.
I’m keen to hear if you found a solution or if either of the above work for you!
LikeLike
should I remove the Switch Port access VLAN from the port
LikeLike
I tried to configure an SG350 and NPS, but it seems the switch don’t use the NPS (on GUI names radius client) for 802.1x port security (I dont’t see any connection request from sg350 however it is an enebled radius client on NPS) what should I do? Thanks in advance
LikeLike
Hi! I’ve not much experience with the SG350, which while it’s Cisco in name I’ve found frustratingly different in the feature set and syntax etc than the bigger brother Cisco products. Doing ‘advanced’ features like this personally would be something I’d do on an enterprise switch rather than the small business switch series just because of the support of such features but in theory if the SG350 says it supports 802.1x on wired then it ought to at least authenticate connected users to a RADIUS / NPS server – but whether it supports the return value from the server to place it into a particular VLAN I’m unsure.
If on the NPS server you’re not seeing the RADIUS request from the switch, assuming the switch is configured correctly for 802.1x on the ports, I’d check the switch can ping the NPS server to confirm default gateways and routing is correct. From there, perhaps run Wireshark on your server to see if the packets are being received to the server but possibly not being processed by the NPS role?
LikeLike
Hello Mike,
First of all thank you for your reply.
In the meantime I tried set up many things and I experienced that if the port use MAC authentication “dot1x authentication 802.1x mac” finally I got authenticate request on my NPS. without this there is no any attempt from switch somehow, I don’t know why… I’m trying to open a ticket by Cisco because I have read by other guys also experience this kind of “issue” (certainly I can’t decide this is a restricted feature or a real issue on smb’s switches)
LikeLike
Hi Mike, Great article. I have followed and it worked like a charm. Only thing that’s not working is Fail Event. I have added the command dot1x authentication-fail vlan # on the Port, but it says on the system that Authentication Failed and it doesn’t get an IP. Any lead on that? Thanks.
LikeLike
Hi Imran,
If the VLAN is explicitly set to be the same # as the fail VLAN do clients still get an IP?
OR if the client fails 802.1x and you set a static IP falling into the fail VLAN range does it then have access?
I’m just wondering if it’s a client issue where it’s not trying to request a new IP on the fail VLAN once authentication fails.
Cheers
Mike
LikeLike